VMware ESXi is mainstream. If you’ve ever deployed a VMware vMA appliance to manage ESXi (or heck, even ESX for that matter), you may have noticed the enforcement of a complex password policy for the vi-admin account. For example, setting a password of password is denied because it is based on a dictionary word (in addition to other morally obvious reasons).
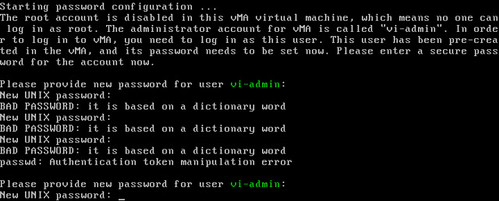
However, you can bend the complexity rules and force a simple password after the initial deployment using sudo. You’ll still be warned about the violation of the complexity policy but by using sudo, the policy is allowed to be bypassed by a higher authority:
sudo passwd vi-admin
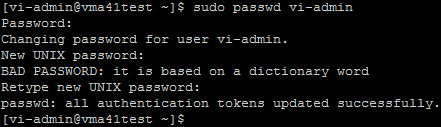
This tip isn’t specific to VMware or the vMA appliance. It is general *nix knowledge. There is ample documentation available which discusses the password complexity mechanism in various versions of *nix. Another approach to bypassing the complexity requirement would be to actually relax the requirement itself but this would impact other local accounts potentially in use on the vMA appliance which may still require complex passwords. Using the sudo command will be faster and leaves the default complex security mechanism in place.
















Thanks for this tip, came in handy today! How incredibly annoying that I had to create a password consisting of about 15 characters with letters, capital letters, numbers, and symbols just to get the vMA running. Thank you VMware for protecting me from myself.
This trick no longer works in vMA 5. Too bad.
yes it does still work in vMA 5.0.. i just used it yesterday.
try Qazx123!#